Security Updates |
||
|---|---|---|
Title |
Date Released |
|
| WannaCry Ransomware | Friday, May 12, 2017 | |
| Bash (Shellshock) Vulnerability | Friday, September 25, 2014 | |
| Internet Explorer Vulnerability | Wednesday, April 30, 2014 | |
| Heartbleed Vulnerability | Wednesday, April 16, 2014 | |
WannaCry Ransomware
As you may have heard through news outlets, a new form of ransomware named WannaCry is currently spreading through computers around the world. This infection can be spread through spam emails containing infected attachments.
As always, we highly encourage you to protect yourself and your data by being especially cautious when opening emails or attachments from unfamiliar sources, especially if these emails are related to job offers, invoices, or prescription drugs. At this time, no Mercer computers have been affected, and your caution is appreciated. If you have any reason to doubt the authenticity of an email, contact the IT Help Desk.
Bash (Shellshock) Vulnerability
Recently, a new security vulnerability affecting the Mac OS X, Linux, and Unix operating systems was discovered. The vulnerability has been named Shellshock, and allows an attacker to remotely execute commands. Apple is aware of the vulnerability and is working quickly to provide a software update for OS X. According to Apple, unless a user configures advanced UNIX services on a Mac, the system is not at risk. A fix has already been provided for Linux operating systems via normal update methods. Microsoft Windows is not affected by this vulnerability. Additional details regarding the impact can be found here.
Internet Explorer Vulnerability
Microsoft announced a security vulnerability affecting all supported versions of Internet Explorer, to include versions 6 through 11. If exploited, this vulnerability could allow remote attackers to gain control of a user's computer. Mercer’s IT department has taken every precaution to prevent the attack from affecting Mercer systems; however, we recommend you take additional precautions until Microsoft releases a patch. We recommend that you only use Internet Explorer for trusted sites. For general Internet use, we recommend the Firefox browser, which should already be installed on your Mercer computer. Mac users are not affected by this issue.
This advisory is also being provided as a courtesy for you as your personal computer systems may not have the protections we have in place at Mercer. Follow the steps below to mitigate the risks to your personal computer:
- Keep Windows Updates current.
- Keep Adobe Flash Updates current.
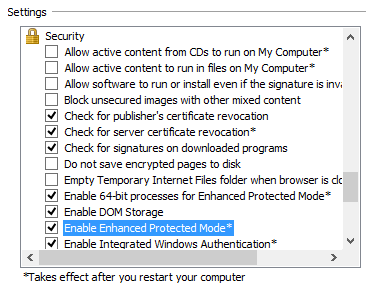
- Run Internet Explorer in “Enhanced Protected Mode” configuration and 64-bit process mode, which is available for IE10 and IE11 in the Internet Options settings:
Additional Information
Micrsoft Security Advisor